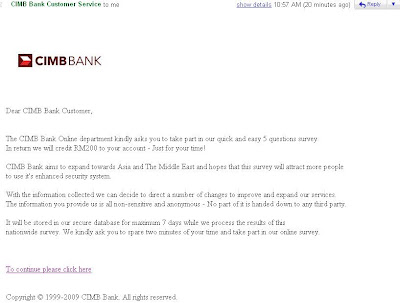
Wednesday, January 20, 2010
Friday, January 15, 2010
Woman loses RM1,900 from Maybank2U
Friday January 15, 2010
Woman loses RM1,900 from online account
By LIM CHIA YING
ONLINE banking is a convenience to many busy people. However, it brought misery to a 26-year-old woman, who wished to be known only as Jenn, who lost RM1,900 from her one-month-old account on Dec 2.
Jenn said the amount was transferred to a third party account without her knowledge after she had logged into the bank’s system using her logon and password.
“One morning in early December, I received an email from Maybank stating that I had a login with an incorrect password in the Maybank system.
“After closing the email, I logged into the system and entered the correct password that it needed.
“However, on the afternoon of the same day, I received an SMS fromMaybank2u.com that RM1,900 from my account that I had opened at the Maybank Taman Midah branch had been transferred to a third party account,” Jenn said at a press conference called by Bukit Bintang MP Fong Kui Lun.
She has since lodged a police report at the Batu 9 Cheras police station.
In the police report, she said when she went to the branch at 2pm the same day, a bank officer named Raymond Lim had given her the funds transfer statement in which she saw that her money had been transferred to an account belonging to a Malay woman named Mayana Muhamad.
Jenn called up the Maybank headquarters to seek an explanation on the issue, and was disappointed that the personnel were not helpful and only provided a written reply to her one month later.
“I had been using another bank, where security was much tighter, before using Maybank’s online banking when I changed job,” she said, adding that she had created the account only in November.
“The RM1,900 was almost all my savings! The officer in the headquarters told me that the police investigation must be completed before action could be taken.
“He also told me that although the bank had contacted the third party, the woman was not cooperating so they could not do anything. Would she cooperate if she is the culprit?” asked the frustrated Jenn, claiming that the bank personnel had even told her there was a queue of other fraud victims.
In Maybank’s written reply to Jenn, virtual banking cyber security manager Baizura Ahmad wrote that following a comprehensive investigation of the said transaction, they had found that a valid user name and password were used to access her account viaMaybank2u.com.
“Our findings revealed that the internet banking username and password were used on Dec 2 to successfully make a login to your Maybank account via Maybank2u.com,” Baizura had stated.
“A Transaction Authorisation Code (TAC) was requested through yourMaybank2u.com account and a valid TAC was successfully sent to your mobile number. This TAC was then used to create a favourite third party account, and subsequently, the amount of RM1,900 was made to the favourite third party account from your account on the same day.
“Based on our investigation into our system, our records showed there was no system failure, problem or any breach of security ofMaybank2u.com in processing the above activities at the mentioned date and time involving the above account.
“In view of this, we very much regret to inform that the bank is unable to accede to your request of the said amount,” the reply said.
In the reply, the bank reiterated that it does not send any email, SMS or make telephone calls to customers to request for personal details, account details of TAC number.
“Customers are also reminded never to disclose their account and banking information to anyone. The bank provides safety information and alerts in Maybank2u.com as well as through our other delivery channels,” the reply stated.
Jenn said she felt helpless on the issue and had since terminated her online account with the bank.
Fong said he would be writing to Bank Negara on the urgent need to monitor the security of online banking.
“Since the matter involved a transfer within the same bank, and the person’s name and account number are known, there is no reason why the bank is unable to do anything.
“The money was transferred without the victim’s knowledge, so it is only right that settlement is made to her.
“I also hope the Finance Minister will respond to this as such a case can result in the public losing confidence in online banking,” he said.
http://thestar.com.my/metro/story.asp?file=/2010/1/15/central/5451096&sec=central